
Over 84,000 Roundcube webmail installations are vulnerable to CVE-2025-49113, a critical remote code execution (RCE) flaw with a public exploit.
The flaw, which impacts Roundcube versions 1.1.0 through 1.6.10, spanning over a decade, was patched on June 1, 2025, following its discovery and reporting by security researcher Kirill Firsov.
The bug stems from unsanitized $_GET['_from'] input, enabling PHP object deserialization and session corruption when session keys begin with an exclamation mark.
Shortly after the patch was released, hackers reverse-engineered it to develop a working exploit, which they sold on underground forums.
Though the exploitation of CVE-2025-49113 requires authentication, attackers claim that valid credentials can be obtained via CSRF, log scraping, or brute-forced.
Firsov shared technical details about the flaw on his blog to help defend against active exploitation attempts that are very likely to occur.
Massive exposure
Roundcube is widely used in shared hosting (GoDaddy, Hostinger, OVH) and government, education, and tech sectors, with over 1,200,000 instances visible online.
Threat monitoring platform The Shadowserver Foundation reports that its internet scans return 84,925 Roundcube instances vulnerable to CVE-2025-49113 as of June 8, 2025.
Most of these instances are in the United States (19,500), India (15,500), Germany (13,600), France (3,600), Canada (3,500), and the United Kingdom (2,400).
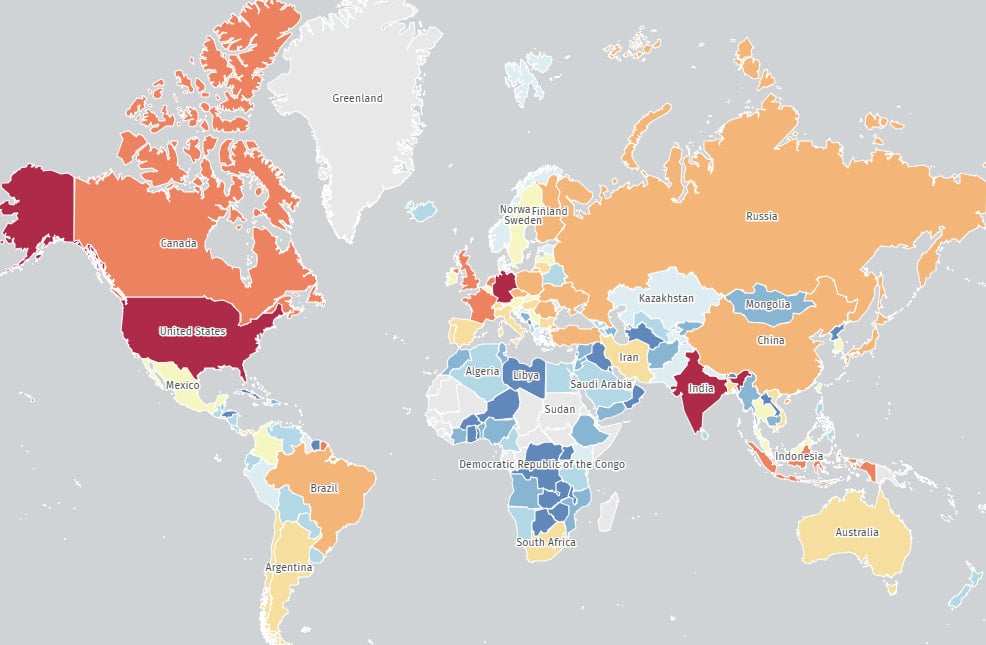
Source: The Shadowserver Foundation
Considering the high risk of exploitation and the potential for data theft, the exposure of those instances is a significant cybersecurity risk.
System administrators are recommended to update to version 1.6.11 and 1.5.10, which address CVE-2025-49113, as soon as possible.
It is unclear if the flaw is being leveraged in actual attacks and at what scale, but immediate action is advised nonetheless.
If upgrading is impossible, it is recommended to restrict access to webmail, turn off file uploads, add CSRF protection, block risky PHP functions, and monitor for exploit indicators.
8 Common Threats in 2025
While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.








Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now