
Slack has enabled a new 'Slack Connect' feature that allows users to send messages or create shared channels with people outside of their organization.
While users had previously been able to test the Slack Connect feature, it has begun to roll out to all paid workspaces today.
"Slack Connect is a new way for organizations to drive business forward and communicate with their customers, partners and vendors as quickly and easily as they interact with their coworkers in Slack," Slack stated in an announcement.
When enabled, Slack users will see a new 'Slack Connect' section in their sidebar, that when clicked on, will display a screen where you can create a shared channel or initiate direct messages with external users.
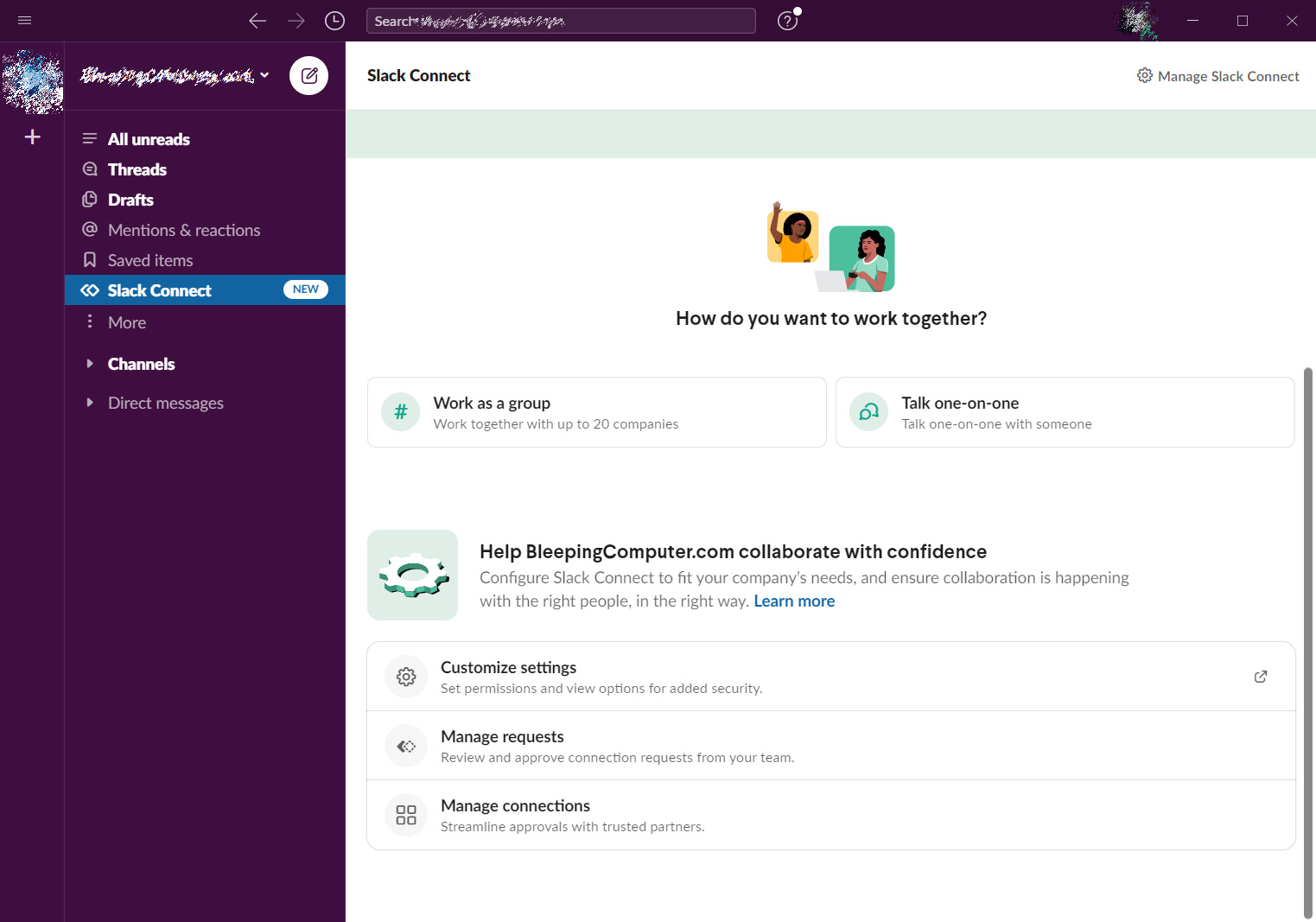
Like other messaging apps, to send DMs, users will first send an invitation to another user by their email address. If the user accepts the invite, a new chat will appear, allowing you to communicate directly with them.
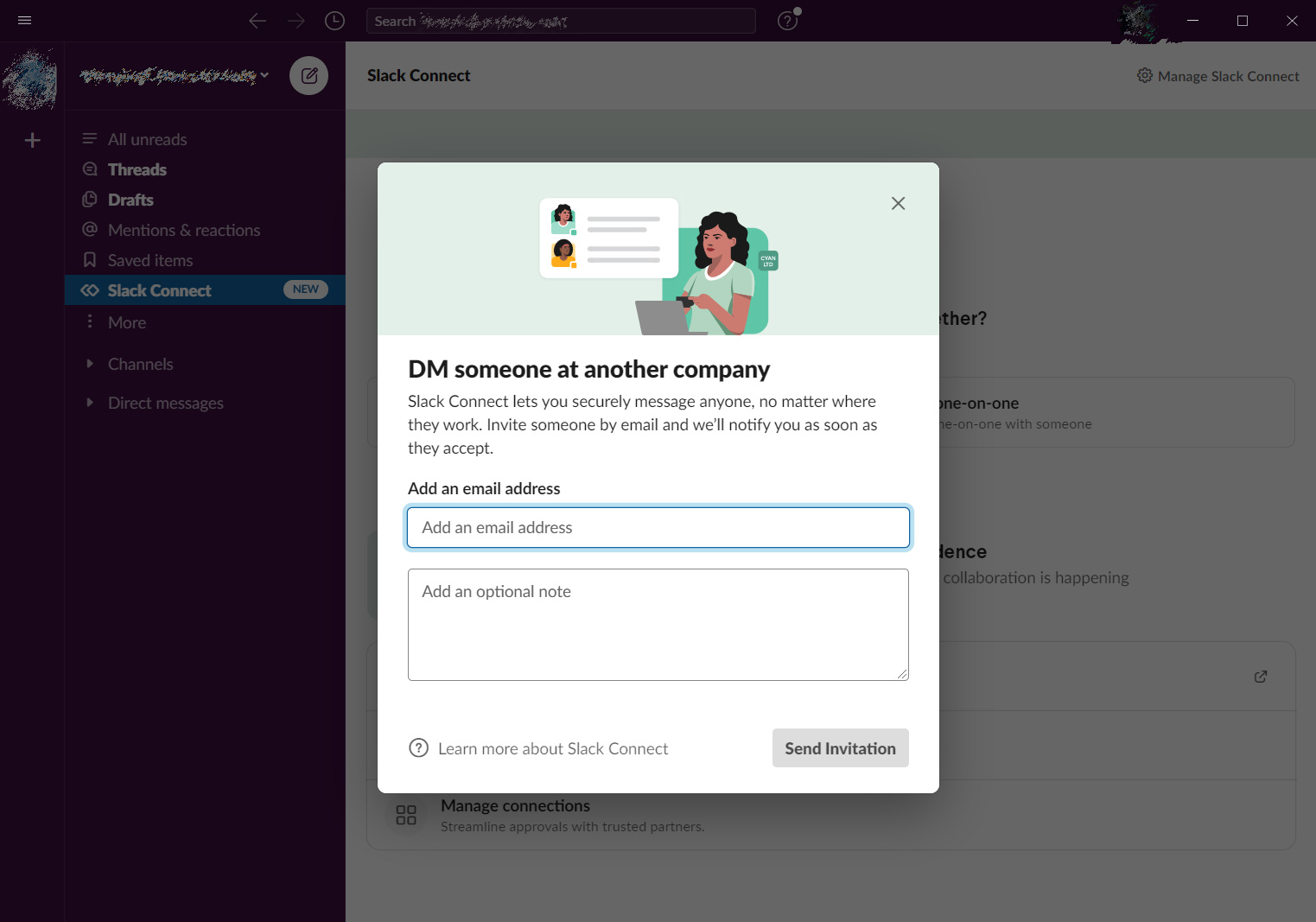
If an organization decides that Slack Connect could lead to security issues or the leaking of confidential information, it is possible to restrict who can use the feature or even disable it completely through the 'Customize Settings' section.
It should be noted that Slack DMs are not end-to-end encrypted. If you are looking for a more secure line of communication, then other messaging apps such as Signal, Wire, or WhatsApp may be a better choice.
Slack disables optional message due to potential abuse
As quickly as the Slack Connect feature launched, Slack has already disabled the optional message to be included in invites as it can be abused for phishing and abusive messages.
When sending a Slack Connect invite, users can add an optional note to be included in the invite to external users.
However, this note can be abused by sending vulgar language or harassing messages to users. As the emails are sent from a generic Slack.com email address, they cannot be easily filtered out without the risk of also filtering legitimate email.
An example of how the Slack Connect invites can be abused is illustrated in the tweet below.
well that was easy as shit to abuse
— Menotti Minutillo (@44) March 24, 2021
- send invite with nasty language
- slack emails you w/ the full content of the invite
- can't block the emails because they come from a generic slack address that informs you of invites
- abuser can keep inviting w/ abusive language https://t.co/Mw9W5L251a pic.twitter.com/dWEAD7ccRO
Another possible way the feature can be abused is by threat actors creating workspaces that imitate legitimate companies. The threat actors can then use these workspaces to target other Slack users with phishing campaigns.
While Slack admins can disable Slack Connect and prevent their users from accepting invites, users will still receive the invite emails unless they are filtered on their mail server.
Update 3/24/21 2:50 PM EST: Updated story about potential for abuse.
8 Common Threats in 2025
While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.








Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now