
The Play ransomware group has developed two custom tools in .NET, namely Grixba and VSS Copying Tool, which it uses to improve the effectiveness of its cyberattacks.
The two tools enable attackers to enumerate users and computers in compromised networks, gather information about security, backup, and remote administration software, and easily copy files from Volume Shadow Copy Service (VSS) to bypass locked files.
Security researchers at Symantec discovered and analyzed the new tools and shared their findings with BleepingComputer before publishing their report.
New custom tools
Grixba is a network-scanning and information-stealing tool used to enumerate users and computers in a domain. It also supports a 'scan' mode that uses WMI, WinRM, Remote Registry, and Remote Services to determine what software runs on network devices.
When performing the scan function, Grixba will check for anti-virus and security programs, EDR suites, backup tools, and remote administration tools. Also, the scanner checks for common office applications and DirectX, potentially to determine the type of computer being scanned.
The tool saves all collected data in CSV files, compresses them into a ZIP archive, and then exfiltrates it to the attackers' C2 server, giving them vital info on how to plan the next steps of the attack.
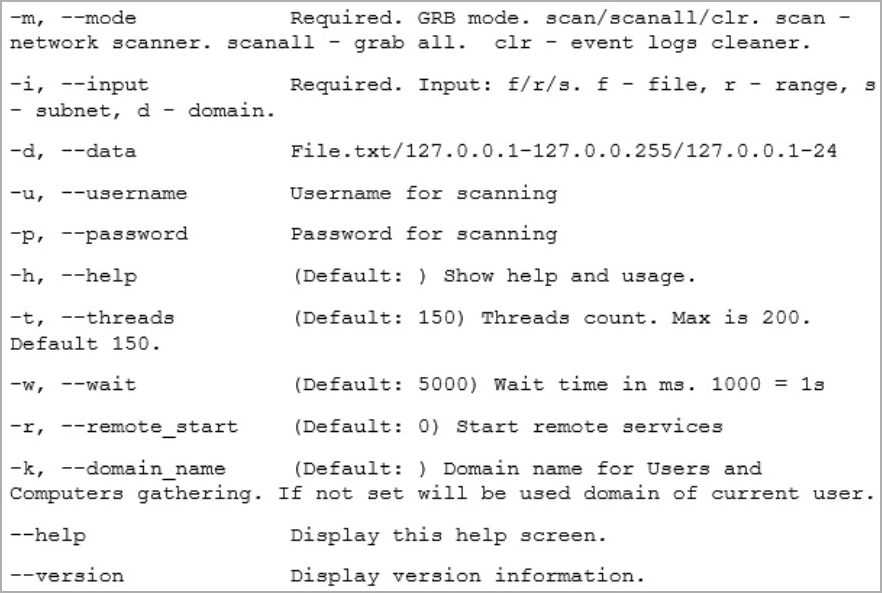
Source: Symantec
The second custom tool spotted by Symantec in Play ransomware attacks is VSS Copying Tool, which allows attackers to interact with the Volume Shadow Copy Service (VSS) via API calls using a bundled AlphaVSS .NET library.
Volume Shadow Copy Service is a Windows feature that allows users to create system snapshots and backup copies of their data at specific time points and restore them in the case of data loss or system corruption.
The VSS Copying Tool enables Play ransomware to steal files from existing shadow volume copies even when those files are in use by applications.
Both tools analyzed by Symantec were written using the Costura .NET development tool, which can build standalone executables that require no dependencies, making it easier to deploy on compromised systems.
Play ransomware's use of custom tools indicates that the notorious threat actor aims to increase the effectiveness of their attacks and carry out their malicious tasks more efficiently.
Since the start of the year, Play ransomware has had several high-profile victims, including the City of Oakland in California, A10 Networks, Arnold Clark, and Rackspace.
8 Common Threats in 2025
While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.









Comments
frostriver - 9 months ago
What does one do if this is happening to them?