
News broke today about "one of the largest data breaches in history," sparking wide media coverage filled with warnings and fear-mongering. However, it appears to just be a compilation of previously leaked credentials stolen by infostealers, exposed in data breaches, and via credential stuffing attacks.
To be clear, this is not a new data breach, or a breach at all, and the websites involved were not recently compromised to steal these credentials.
Instead, these stolen credentials were likely circulating for some time, if not for years. It was then collected by a cybersecurity firm, researchers, or threat actors and repackaged into a database that was exposed on the Internet.
Cybernews, which discovered the briefly exposed datasets of compiled credentials, stated it was stored in a format commonly associated with infostealer malware, though they did not share samples
An infostealer is malware that attempts to steal credentials, cryptocurrency wallets, and other data from an infected device. Over the years, infostealers have become a massive problem, leading to breaches worldwide.
These types of malware impact both Windows and Macs, and when executed, will gather all the credentials it can find stored on a device and save them in what is called a "log."
An infostealer log is generally an archive containing numerous text files and other stolen data. The text files contain lists of credentials stolen from browsers, files, and other applications.
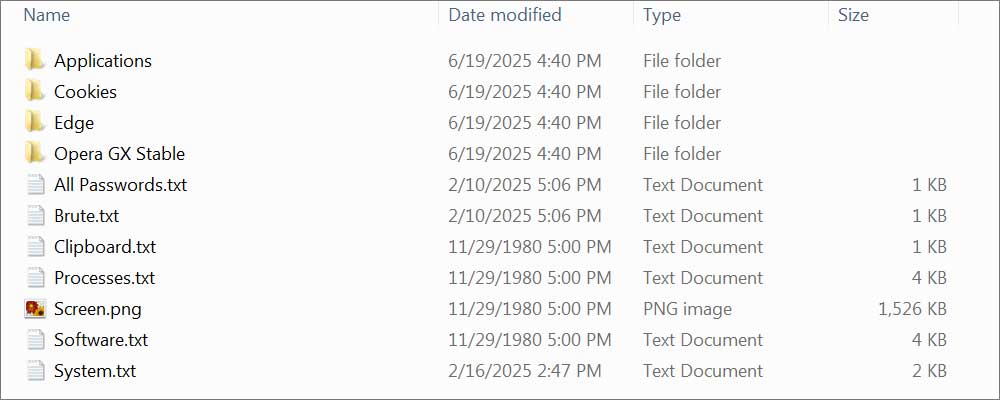
Source: BleepingComputer
Stolen credentials are usually saved one per line in the following format:
URL:username:password
Sometimes, the delimiter between each component is changed to a comma, semicolon, or dash.
For example, the following is how an infostealer will save credentials stolen from a device to a log:
https://www.facebook.com/:jsmith@example.com:Databr3achFUd!
https://www.bank.com/login.php:jsmith:SkyIsFa11ing#
https://x.com/i/flow/login:jsmith@example.com:StayCalmCarryOn
If someone is infected with an infostealer and has a thousand credentials saved in their browser, the infostealer will steal them all and store them in the log. These logs are then uploaded to the threat actor, where the credentials can be used for further attacks or sold on cybercrime marketplaces.
The infostealer problem has gotten so bad and pervasive that compromised credentials have become one of the most common ways for threat actors to breach networks.
We have a webinar next month titled "Stolen credentials: The New Front Door to Your Network" that focuses on infostealers, compromised credentials, and how organizations can protect themselves.
This problem has also led law enforcement worldwide to actively crack down on these cybercrime operations in recent actions, such as "Operation Secure" and the disruption of LummaStealer.
As infostealers have become so abundant and commonly used, threat actors release massive compilations for free on Telegram, Pastebin, and Discord to gain reputation among the cybercrime community or as teasers to paid offerings.
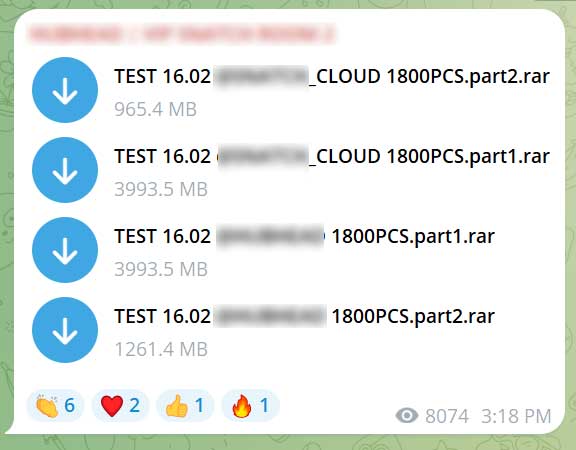
Source: BleepingComputer
To see how many passwords are given away for free, the single 1,261.4 MB file in the image above contained over 64,000 credential pairs.
There are thousands, if not hundreds of thousands, of similarly leaked archives being shared online, resulting in billions of credentials records released for free.
Many of these free archives were likely compiled into massive data sets that were briefly exposed and seen by Cybernews.
Similar credential collections were released in the past, such as the RockYou2024 leak, with over 9 billion records, and "Colection #1," which contained over 22 million unique passwords.
Despite the buzz, there's no evidence this compilation contains new or previously unseen data
What should you do?
So, now that you know there was a massive leak of credentials likely stolen through infostealers, data breaches, and credential-stuffing attacks, you may be wondering what you should do.
The most important step is to adopt and maintain good cybersecurity habits you should already be following.
If you're concerned that an infostealer might be present on your computer, scan your device with a trusted antivirus program before changing any passwords. Otherwise, newly entered credentials could be stolen as well.
Once you're confident your system is clean, focus on improving your password hygiene.
That means using a unique, strong password for every site you use, and relying on a password manager to keep them organized and secure.
However, even unique passwords won't help you stay protected if you are hacked, fall for a phishing attack, or install malware.
Therefore, it is crucial that you also use two-factor authentication (2FA) along with an authentication app, like Microsoft Authenticator, Google Authenticator, or Authy, to manage your 2FA codes. Some password managers, like Bitwarden and 1Password, also include authentication functionality, allowing you to use one application for both.
With 2FA enabled, even if a password at a site is compromised, threat actors cannot access the account without your 2FA code.
As a general rule, you should avoid using SMS texts to receive 2FA codes, as threat actors can conduct SIM-swapping attacks to hijack your phone number and obtain them.
As for this leak, with this many credentials leaked, there is a chance one of the readers of this article will be listed in the compilation.
However, don't panic and stress about it, running around changing all your passwords. Instead, take this opportunity to improve your cybersecurity habits.
To check if your credentials have appeared in known breaches, consider using services like Have I Been Pwned.
And if you use the same password across multiple sites, now is the time to switch to unique ones.
That way, leaks like this become far less dangerous to you.
Update 6/20/25 10:08 PM EST: Article updated to clarify that this was multiple datasets found rather than a single database and to remove "mother of all breaches," as that was to describe the other compilation discovered in 2024.
8 Common Threats in 2025
While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.








Comments
Elastoer - 2 weeks ago
I have migrated most of my daily life off of the Internet at this point. As of now, I only use a computer when I absolutely have to. I now have physical copies of all my vital records, which will never get put on an Internet connected device. I also have a very small number of online accounts, and I think long and hard before creating any additional ones.
pnda73 - 2 weeks ago
The original source cybernews, has updated their article with a few screenshots as proof that the data dump contains new credentials.
Lawrence Abrams - 2 weeks ago
The screenshots prove the data exists but not whether it's new data.
In fact, the dataset names indicate that they are just collections of credentials, aka txtbases.
pnda73 - 2 weeks ago
I know anyone can show off data and it doesn't mean it's new, but all the credentials in the screenshots have timestamps of 2025.
Please explain how the timestamps are new, but you think the credentials aren't. To me (and maybe other viewers) this is the crux of the proof and pivotal point of concern (assuming cybernews didn't generate bogus data).
Thank you for your time.
Lawrence Abrams - 2 weeks ago
Timestamps may not be for when they were stolen, but when they were ingested into the collection/database. Hard to tell with redacted info.
I don't think they tampered or generated bogus data. The person who found the data sets, Bob Diachenko, is a known and trusted researcher and wouldn't do that.
Also, read this from Hudson Rock, a company who focuses on this type of data: https://www.infostealers.com/article/16-billion-credentials-leak-a-closer-look-at-the-hype-and-reality-behind-the-massive-data-dump/
Edited to add, that for those who are concerned it's new credentials, there is nothing wrong with rotating your passwords. It's only going to make you more secure.
Mr_Robot - 1 week ago
If Bob Diachenko is trusted researcher, why he is stating it is new breach then? Based on cybernews article he is contributing to cybernews as well. So he should stop them, or not reposting that article on his LinkedIn.
Just wondering, because I'm confused by all those statements. All those supporting this is new breach vs those don't support that theory.
However, Have I Been pwned didn't report anything yet, so I believe it is not new breach.
h_b_s - 1 week ago
Its impossible to know whether the data is new or old, mostly old with some new, or whatever mix without knowing the database field contexts. The formatting suggests this dump is a conglomeration of multiple datasets collected over time. You can tell because of the differences in delimiters - something no one implementing a coherent text CSV-style database from scratch does.
Date/timestamps without context are meaningless. These could be creation dates or modification dates. Creation dates are sometimes dependable, but we have no way of knowing that's what these are or how they were created which means even file creation dates can be wrong. Some may be, some may not, or none may be. Modification stamps are unreliable since just reading or "touching" (executing a write op without alteration) an entry, depending on the database or schema used, can alter the stamp, making modification stamps only useful for debug purposes - but again, context is missing making the dates useless. Its dangerous to take time stamps at face value and futile without context.
KuraBee - 1 week ago
"To check if your credentials have appeared in known breaches, consider using services like Have I Been Pwned": that's actually incorrect, HIBP informs you about leaked *emails*, not email + password pairs.
If you're interested in leaked credentials, check sites like https://scatteredsecrets.com/.
Winston2021 - 1 week ago
"a compilation of previously leaked credentials"
I've always wondered why hackers wouldn't have taken all of the copious amount of data leaked and cross-correlated it to come up with a "cleaner" list where multiple leaks had some of the same data and that was then used to add any additional details available to any "validated" contents.
Looks like they may have in this case.